Clickjacking
Theory
Lots of websites allow to browsers to render them in a <frame>, <iframe>, <embed> or <object>. This allows attackers to "load" the website in a transparent layer and trick users into thinking they are browsing the legitimate website. This allows attackers to "hijack" their clicks and make them do something else (Twitter worm, Facebook likes).
HTTP security headers like XFO (X-Frame-Options) and CSP (Content-Security-Policy) mitigate clickjacking attacks.
Practice
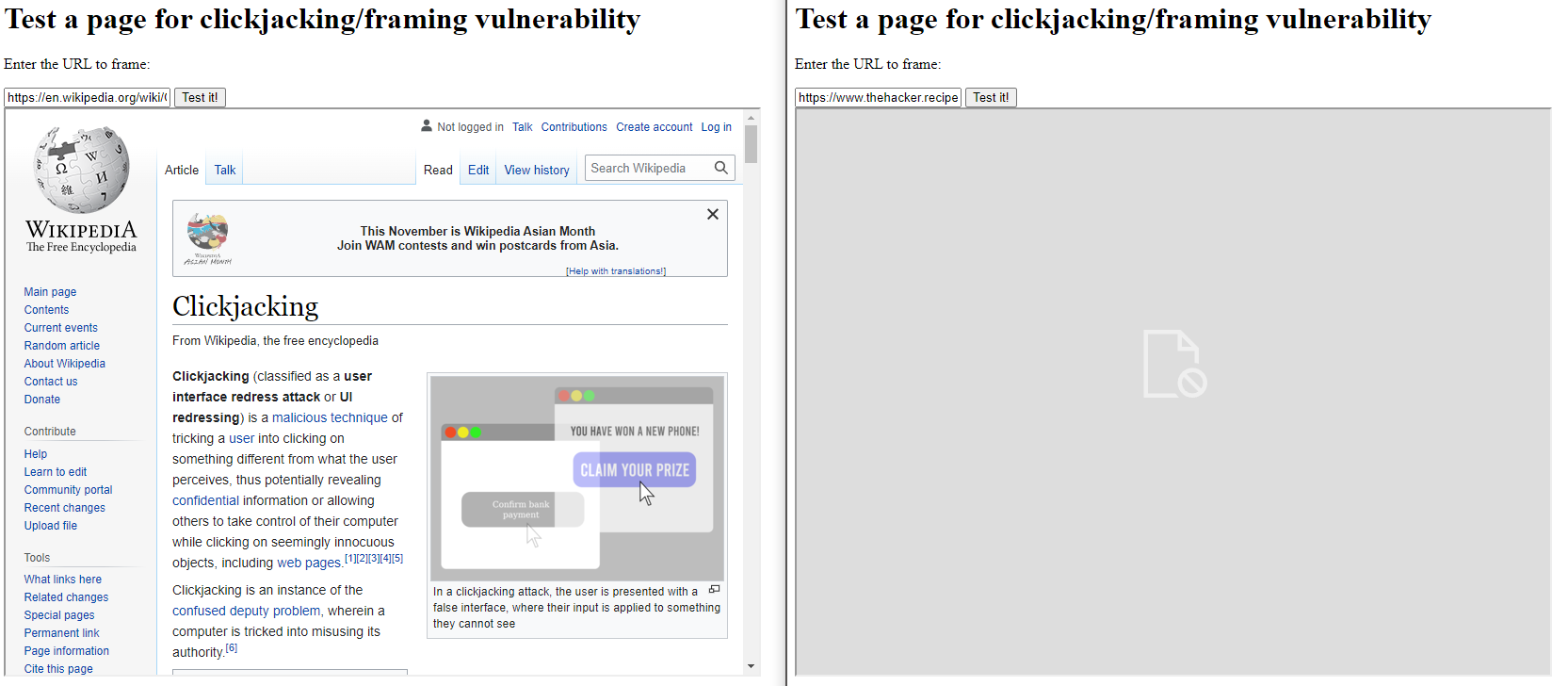 (left) vulnerable | not vulnerable (right)
(left) vulnerable | not vulnerable (right)
The following HTML code can be used in a browser to attempt a clickjacking on a target URL.
<html>
<head>
<title>Clickjacking / framing test</title>
</head>
<body>
<h1>Test a page for clickjacking/framing vulnerability</h1>
<p>Enter the URL to frame:</p>
<input id="url" type="text" value="http://TARGET.com"></input>
<button id="submit-test" onclick='document.getElementById("iframe").src=document.getElementById("url").value'>Test it!</button>
<br />
<br />
<hr>
<br />
<iframe src="about:blank" id="iframe" width="100%" height="75%"></iframe>
</body>
</html>